Now Maybe Taiwan Will Take Cybersecurity Seriously
(Bloomberg Opinion) -- I was at a hackers conference in Taipei a few years ago when I got talking to one of the country’s leading cybersecurity experts. I wanted to know the state of play in the ongoing cyber war between Taiwan and China.
“There’s no war,” came the response. I was flummoxed. All day, stories had been flowing about attacks from China and the ongoing risks.
“It’s only a war if you fight back,” was the explanation. “Taiwan doesn’t fight back.”
For more than a decade, Taiwan has been ground zero for attempts to breach its computer networks. Beyond obvious targets such as political parties, government departments and national security apparatuses, many businesses have been attacked. In one breach, a major flat-panel display maker’s patent department was infiltrated, and all the evidence pointed to Chinese hackers.
Security specialists around the world turn to small independent teams in Taiwan for advice on the latest techniques, because quite often, it’s the first to be targeted by new tools and methods developed by mainland hacker armies.
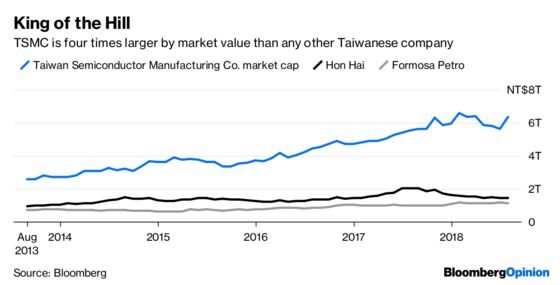
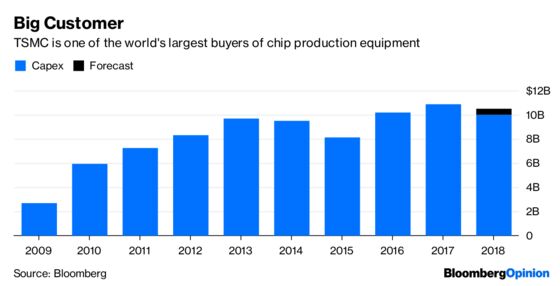
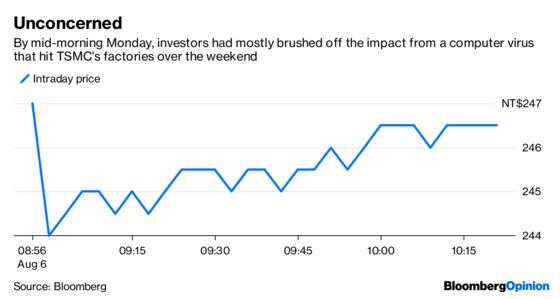
This brings me to Taiwan Semiconductor Manufacturing Co., which this morning is mopping up after a virus spread among its production facilities over the weekend. The company expects a real financial hit, saying:
We estimate the impact to third-quarter revenue to be about 3 percent, and the impact to gross margin to be about one percentage point.
Security experts are no doubt swarming over TSMC’s factories, analyzing the code and seeking to understand its origins. TSMC believes its network systems weren’t breached, and that it wasn’t specifically or maliciously targeted. It wasn’t a hack, executives said. I believe them. Which is to say, I believe that they believe that.
And yet, it appears lines of code were deliberately written for semiconductor production machinery with the intent of causing havoc. This virus somehow made it onto at least one piece of equipment that was then placed inside TSMC factories, and because of what appears to be poor execution of the company’s installation protocol, the virus wasn’t found or isolated, and instead spread via internal networks to other production facilities.
Perhaps the virus writer was some script kiddie in Europe who never imagined his code would make it into the wild. Maybe someone wanting to fool around was throwing her software all over the place and it just happened to stick on this piece of machinery.
Or perhaps there’s a state actor known to be targeting Taiwan’s key industries. One that’s already shown its willingness to go to extraordinary lengths to breach specific companies globally. Maybe that organization got lucky in that this code found its way into the fabs of Taiwan’s most-important company, instead of some lesser-known chipmaker elsewhere.
Twelve months ago, Taiwan suffered blackouts that impacted some areas. I wrote a column relaying the anecdote of a friend who’d wished that TSMC had been impacted (it wasn’t), because only then would the government be spurred into action to fix a looming power crisis that threatens the island’s economy and security.
A similar kind of schadenfreude comes to mind here. Maybe TSMC is the victim of some software stupidity. Maybe I’m getting ahead of myself and have been influenced by too many stories of corporate targets from various state actors’ ongoing cyber campaigns.
Or maybe, like the impending power crisis, TSMC is the canary in the coalmine, and Taiwan needs to take a hitherto hidden problem seriously.
To contact the editor responsible for this story: Katrina Nicholas at knicholas2@bloomberg.net
This column does not necessarily reflect the opinion of the editorial board or Bloomberg LP and its owners.
Tim Culpan is a Bloomberg Opinion columnist covering technology. He previously covered technology for Bloomberg News.
©2018 Bloomberg L.P.