(Bloomberg Opinion) -- Oil pipelines, banks, internet networks, hospitals, manufacturing plants, water-treatment systems. We don’t have to imagine the damage hackers could wreak by paralyzing just one of these gears in the larger U.S. economic engine — we’re seeing it play out this week at the gas pump. Often all it takes is an oblivious worker clicking a tainted e-mail link, or an IT department getting momentarily lazy about computer-system hygiene. While we don’t know exactly what led to the Colonial Pipeline ransomware attack, it’s a reminder that every digitally connected company has vulnerabilities and that critical U.S. infrastructure makes for the juiciest target.
For a business that transmits fuel throughout the U.S. Gulf Coast and East Coast, it’s easy to see how cybersecurity might slip down the list of concerns. Managers have to regularly worry about repairs to prevent oil leaks, on-the-job accidents, natural disasters, as well as pandemics — all risks listed in the annual filings of publicly traded pipeline operators. But devoting resources to cybersecurity now can save you a lot later.
Just ask Colonial: The company quietly paid nearly $5 million in untraceable cryptocurrency to Eastern European hackers last Friday to gain back control of its systems, according to Bloomberg News, an amount that in itself may be minuscule compared with the cost of disruption from the pipeline’s shutdown. That’s after the Associated Press reported that an outside audit of Colonial in 2018 found “glaring deficiencies” in its data-management practices. It just so happens the company was looking to hire a new cybersecurity manager two months ago.
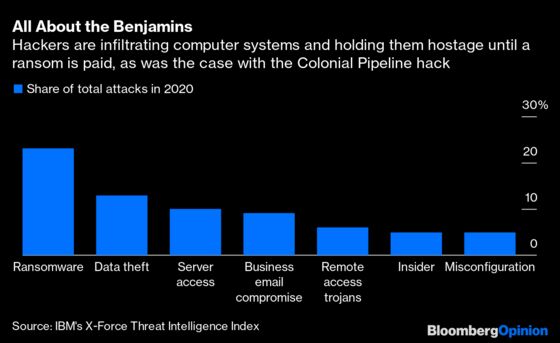
Almost 80% of all breaches have a financial motive, said Sampath Sowmyanarayan, chief revenue officer for Verizon Business, which has a team that studies cybersecurity breaches in partnership with the FBI. “It’s almost always about the money,” he said. After all, in a ransomware attack, the key word is ransom.
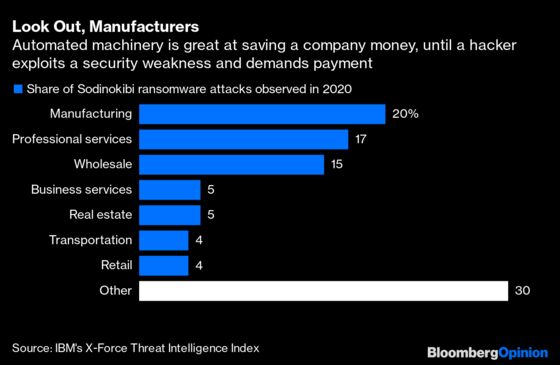
Colonial isn’t alone in neglecting its digital health. Small energy companies spend only about 0.25% of their revenue on security, Brian Walker, a principal at risk-advisory firm The CAP Group in Dallas, told Bloomberg News. Big tech companies and banks spend about 1.5%, and that’s off of much larger sums of money. Chief executive officers everywhere should take this as a wake-up call; in recent years, big stock-buyback programs have pointed to companies generating so much extra cash they don’t know how else to spend it. Shareholders would much less prefer to see money spent recovering from a breach that better vigilance might have prevented, and at a much lower cost.
Data breaches cost companies $3.86 million per incident on average last year, though for entities without advanced-security automation the damage was even greater at $6.03 million, according to an International Business Machines Corp. report. Colonial’s $5 million ransom payment may sound like a lot, but — please cover your ears, hackers — it’s not hard to imagine demands going much higher when nationally important and societally necessary infrastructure is involved that’s known to generate billions of dollars a year in profits.
Still, “advanced security” shouldn’t elicit Hollywood images of retinal scanners opening secret rooms full of expensive high-tech equipment. In reality, the front line of protecting against computer-system threats is much more basic: Teach your employees not to be so cavalier in their clicking and sharing. “The James Bond stuff is pretty small in the scheme of things,” said Verizon’s Sowmyanarayan.
The biggest entryways for breaches these days are phishing — e-mails purporting to be from a legitimate source that steal information from unsuspecting users — and social engineering. An example of the latter is a caller pretending to be from the Internal Revenue Service and asking you to confirm your Social Security number as they build a profile of you. Or maybe the caller purports to be your employer wanting to confirm your login credentials. Sometimes the scam is obvious, but other times hackers can be very convincing.
Remote work has also presented new risks. Hackers in February exploited the remote-access software of an Oldsmar, Florida, water-treatment facility, which was using an outdated computer system and reusing passwords, in an attempt to poison the water with dangerously high levels of sodium hydroxide. Thankfully, an alert worker quickly intervened.
A natural question that’s arisen from the Colonial attack is whether government needs to play a more direct role in cybersecurity supervision of critical infrastructure owned by the private sector. In this divisive political environment, that would be a lively debate, and it’s clear what big business would say. However, the U.S. National Institute of Standards and Technology, an agency of the Department of Commerce, does provide a cybersecurity framework, which Verizon recommends to its business customers. Among other things, it stresses workforce training. Some companies may go so far as to develop their own internal phishing attempts to test employees. The click rate in phishing simulations is down to 3%, but “there’s a long tail of companies with far larger click rates,” according to Verizon’s 2021 Data Breach Investigations Report.
Other good habits include backing up data, ensuring network packets are updated, auditing logs and application “whitelisting” so that users can only access programs approved by the administrator, Sowmyanarayan said. It’s no wonder the information-security team at Verizon Media Group (also known as Yahoo and AOL) calls themselves The Paranoids.
The terror attacks on Sept. 11, 2001, made organizations rethink security. The Covid-19 pandemic forced stricter health and sanitation protocols. It would be a mistake to treat the Colonial Pipeline hack any differently when it comes to cybersecurity.
As a side note, the use of cryptocurrency as ransom only bolsters the case of crypto critics such as Berkshire Hathaway Inc. Vice Chairman Charlie Munger, who most recently said he doesn't "welcome a currency that's so useful to kidnappers and extortionists."
This column does not necessarily reflect the opinion of the editorial board or Bloomberg LP and its owners.
Tara Lachapelle is a Bloomberg Opinion columnist covering the business of entertainment and telecommunications, as well as broader deals. She previously wrote an M&A column for Bloomberg News.
©2021 Bloomberg L.P.