Hackers Pose as Flirty Aerobics Instructor to Target Employees
Hackers Pose as Flirty Aerobics Instructor to Target Employees
(Bloomberg) -- A hacking group aligned with Iran’s government has waged a years-long campaign to steal data from American defense contractors, even posting as a flirtatious aerobics instructor from the U.K. in an attempt to dupe an employee, according to cybersecurity researchers.
The group, known as TA456 or Tortoiseshell, has sought out smaller subsidiaries and contractors in an effort to use them as a launching pad to compromise larger defense companies through the supply chain, according to a report published Wednesday by the Sunnyvale, California-based cybersecurity firm Proofpoint Inc.
The hackers are one of the most resourceful Iran-linked hacking groups Proofpoint has tracked, due to their persistence over long periods of time and the methods they use to trick people, said Sherrod DeGrippo, Proofpoint’s senior director of threat research and detection. “This campaign demonstrates that even after an individual is targeted by a persona, it can take months or years for TA456 to attempt to deliver malware,” DeGrippo said.
The security firm declined to identify names of people or companies that had been targeted.
Iran’s Foreign Ministry didn’t respond to a message seeking comment.
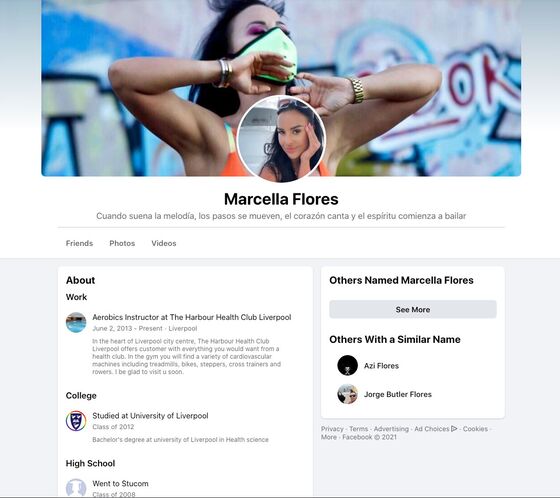
The researchers found evidence that the Iranian hacker group created a persona called Marcella Flores, who posed as a glamorous aerobics instructor and university graduate from Liverpool, England. Operating on Facebook and other social media websites, the hackers operating the Flores account cultivated relationships with targeted employees, before attempting to secretly compromise their computers, according to Proofpoint.
In one case, between November 2020 and June 2021, the hackers used the Flores persona to send benign messages, photographs and a coquettish video to an intended victim who worked for a subsidiary of an aerospace defense contractor. After attempting to build a trusted relationship, the Flores account sent a fake “diet survey” about eating habits that was laced with malware that could steal usernames, passwords and other data from the infected computer. The email was signed “Marcy.”
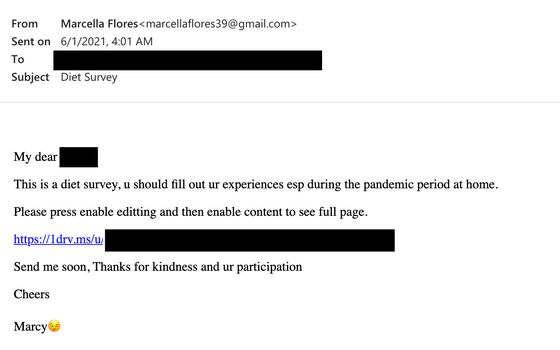
It wasn’t clear if the hackers successfully obtained any data from the targeted aerospace employee. However, Proofpoint said its security software had blocked the hackers’ links to download the malicious files.
Both Proofpoint and Facebook concluded the Flores account was fake.
On July 15, Facebook removed the Flores account from its platform in a coordinated takedown of users linked to Iranian hacker activity. Facebook said at the time that the accounts it removed were linked to a hacking group it identified as Tortoiseshell, which had targeted military personnel and companies in the defense and aerospace industries primarily in the U.S., the U.K. and Europe. “This group used various malicious tactics to identify its targets and infect their devices with malware to enable espionage,” Facebook said in a statement.
Facebook attributed a portion of Tortoiseshell’s activity to Mahak Rayan Afraz, an Iranian IT company with alleged ties to the Islamic Revolutionary Guard Corps. The group was previously identified targeting information technology providers in Saudi Arabia “in what appear to be supply chain attacks with the end goal of compromising the IT providers’ customers,” according to a September 2019 report from the security firm Symantec.
Mahak Rayan Afraz didn’t immediately respond to a request for comment.
©2021 Bloomberg L.P.